Before Android 7, all apps automatically trusted user-installed certificates by default, making the inspection of HTTPS traffic relatively straightforward. One could simply install a self-signed certificate into the system, and apps would automatically trust that certificate. Subsequently, an MITM (man-in-the-middle) proxy, such as Charles or Fiddler, could be initiated to monitor the decrypted HTTPS traffic using the installed certificate.
However, starting with Android 7, only system certificates are trusted by default, which means that HTTPS traffic inspection no longer works by installing additional certificates that land in the user certificate store. Although apps can be configured to trust them, very few apps actually do so.
With a growing number of apps discontinuing support for older Android versions, and devices running Android prior to 7 becoming increasingly rare, monitoring HTTPS traffic on Android devices has emerged as a significant challenge in recent times.
This article covers a method to overcome this obstacle. It has minimal device limitations, and anyone can achieve it with a computer.
The primary challenge lies in making the system trust your certificate. To accomplish this, root privilege is required on Android 7+ systems, but rooting an actual device can be problematic and risky. Fortunately, many Android emulators support root mode out of the box and provide easy installation as well.
TL;DR
- Get the certificate from the MITM proxy (e.g., Charles).
- Use an Android emulator (e.g., MEmu, MuMu), and turn on root access.
- Use
adbto push the certificate into the system certificate store. - Configure the MITM proxy as usual.
- Configure the Android system network proxy to be the MITM proxy port.
- Start capturing.
This blog post uses Charles and MEmu as an example.
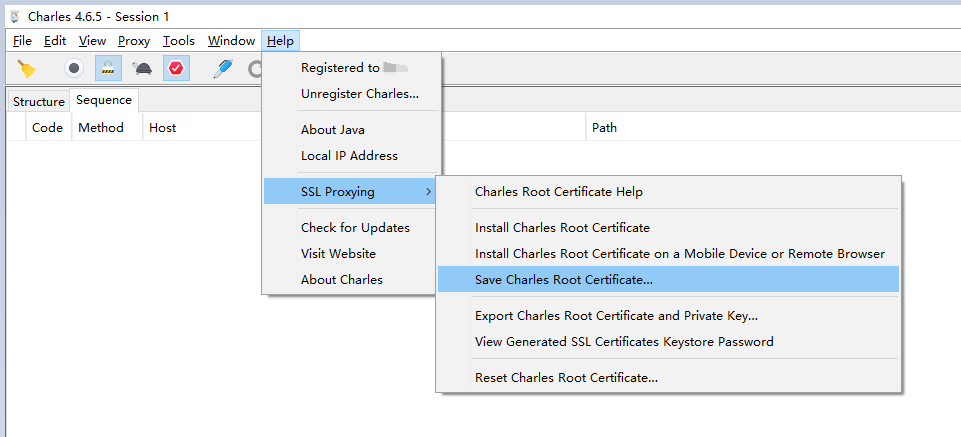
Save the root certificate
In Charles, save the root certificate to somewhere on your computer.
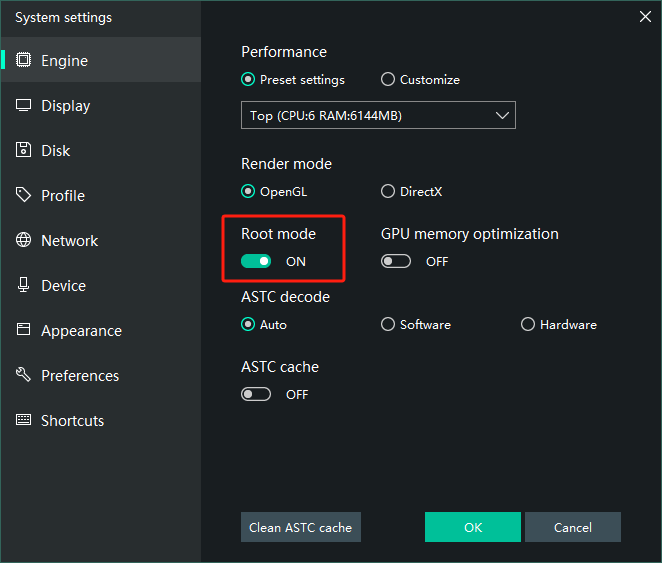
Turn on MEmu Root mode
Ensure that the Root mode is on in MEmu's "System settings"
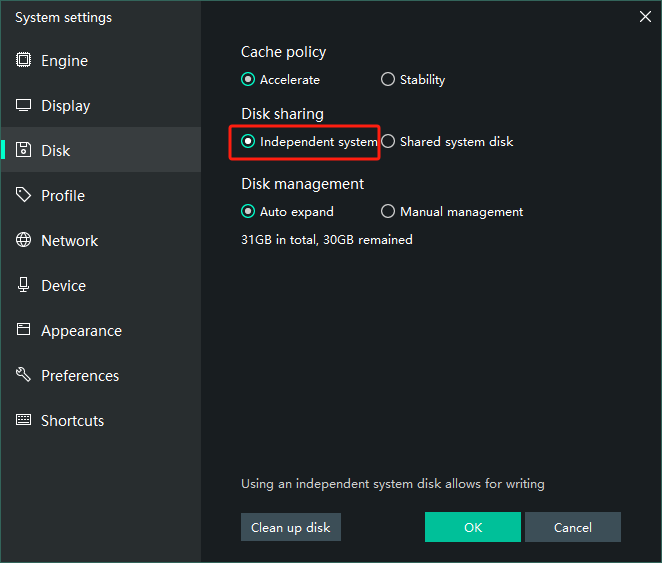
Switch disk sharing mode to "Independent system", in order to enable write permission to /system
Push the certificate into the system
First, get a hash code of the previously saved certificate.
openssl x509 -subject_hash_old -in /path/to/your/certificate.pem | head -1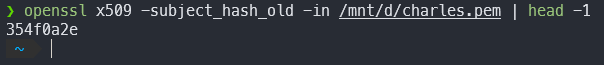
For Windows users, you may either run it under a UNIX environment (e.g., Ubuntu on WSL2, VirtualBox, standalone Linux or Mac machines, etc), or install Win32/Win64 OpenSSL.
Rename the certificate as the output hash with the extension 0
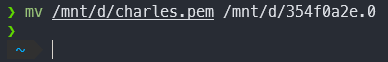
Get root access to the system with adb, you can use your own adb or the one shipped with MEmu. It is located in the MEmu root folder.
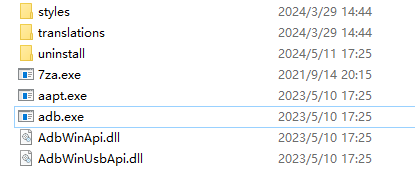
Open a terminal under the folder. Enter the following commands. (Replace <renamed_certificate> with the certificate file name you just renamed.)
./adb root
# A prompt may appear in the Android screen, click Allow
./adb shell "mount -o rw,remount /system"
./adb push /path/to/the/<renamed_certificate> /system/etc/security/cacerts
./adb shell "chmod 664 /system/etc/security/cacerts/<renamed_certificate>"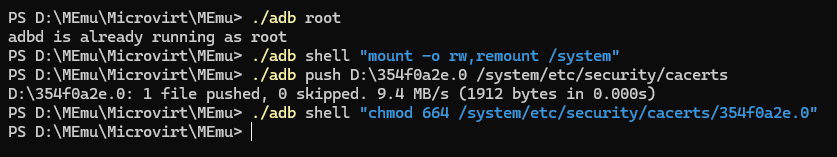
Our certificate is now installed properly!
Setup Charles
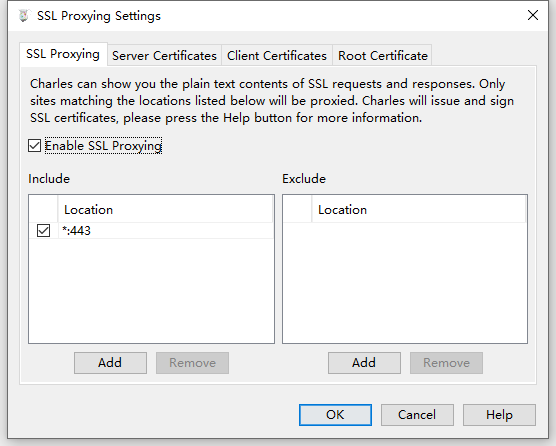
In Charles menu. Open "Proxy" -> "SSL Proxying Settings". Click "Enable SSL Proxying". Make sure the default "Location" in the "Include" section is also checked.
Open "Proxy" -> "Proxy Settings". Make sure the HTTP Proxy port is 8888.
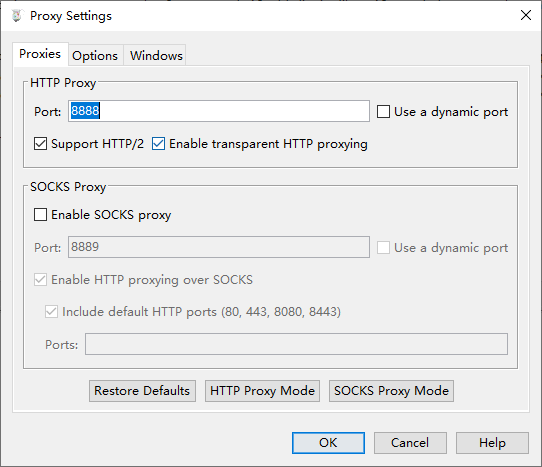
Click "Proxy" -> "Start Recording".
Setup an Android emulator
In MEmu system settings, navigate to "Network & internet" -> "Wi-Fi". Click the connected Wi-Fi. Click "Advanced" option here.
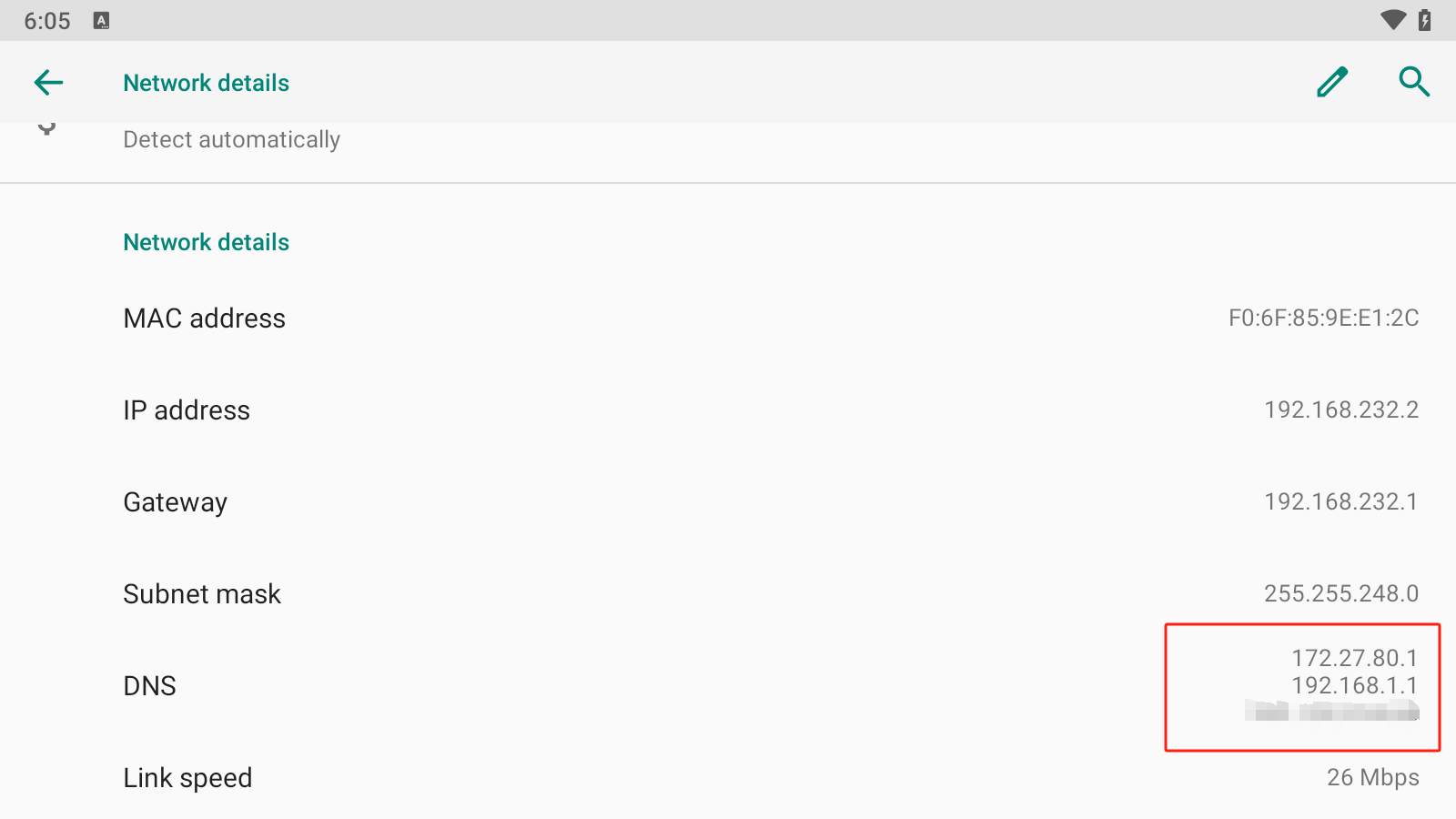
In the DNS section, remember the first IP address, which can be used to access Charles proxy port on the host system. In my case, it's 172.27.80.1. This IP can vary from different Android emulators. For example, the IP is 10.0.2.2 for the emulator in Android Studio.
On the same page, click the edit button in the top right corner.
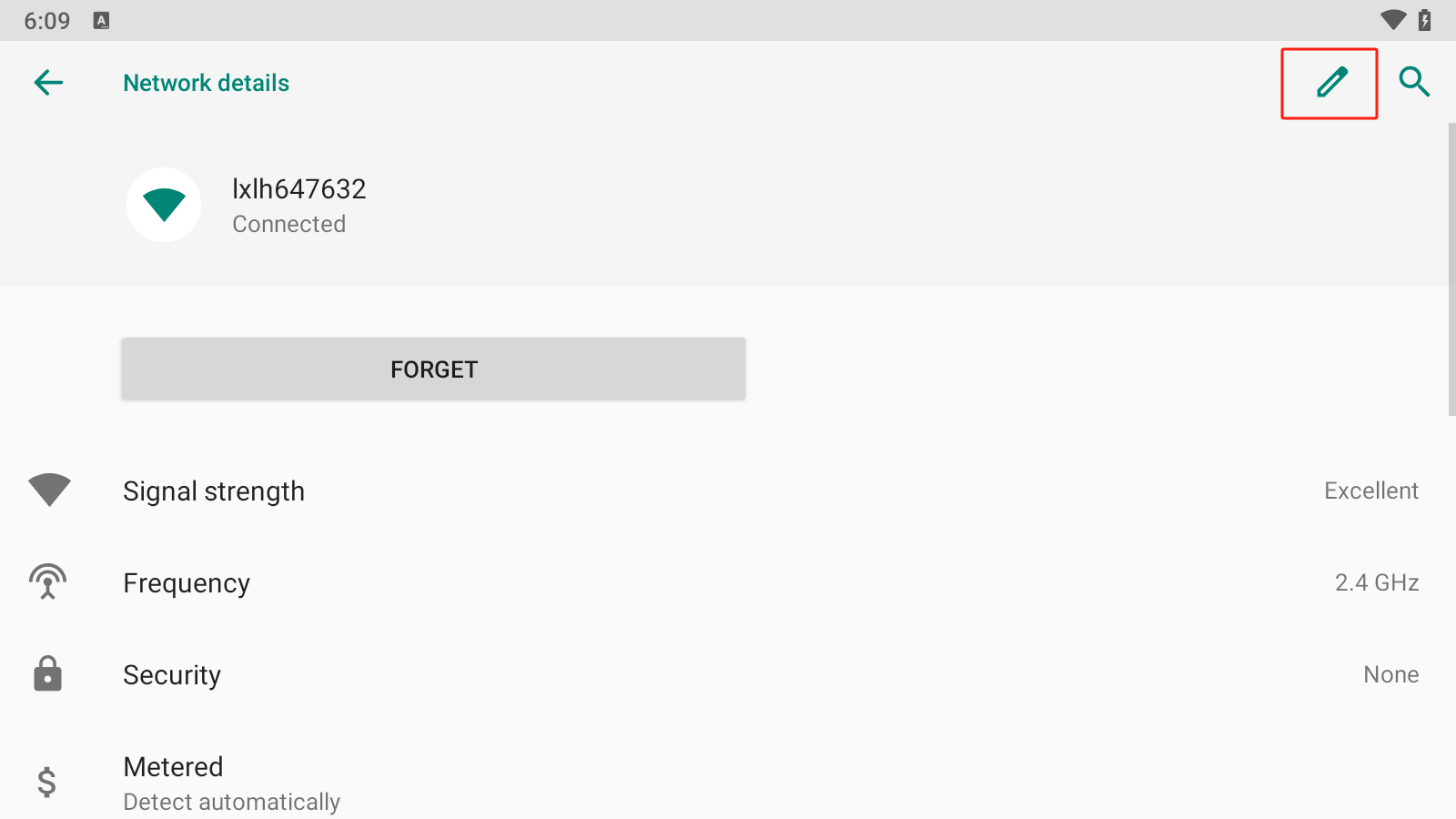
Expand the "Proxy" dropdown menu, click "Manual". Input the IP we just remembered in "Proxy hostname", and enter 8888 in "Proxy port". Click "Save".
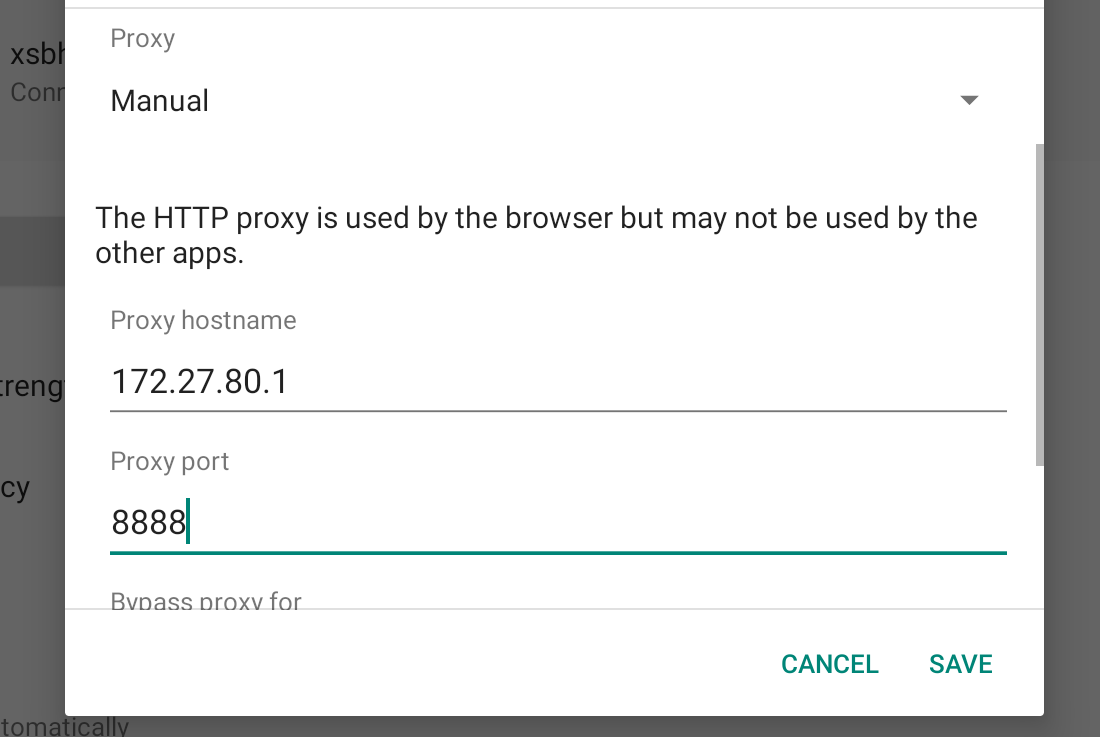
Happy capturing!
Everything is set. Now, open an app, say Booking.com, and you should see https traffic showing on the list.
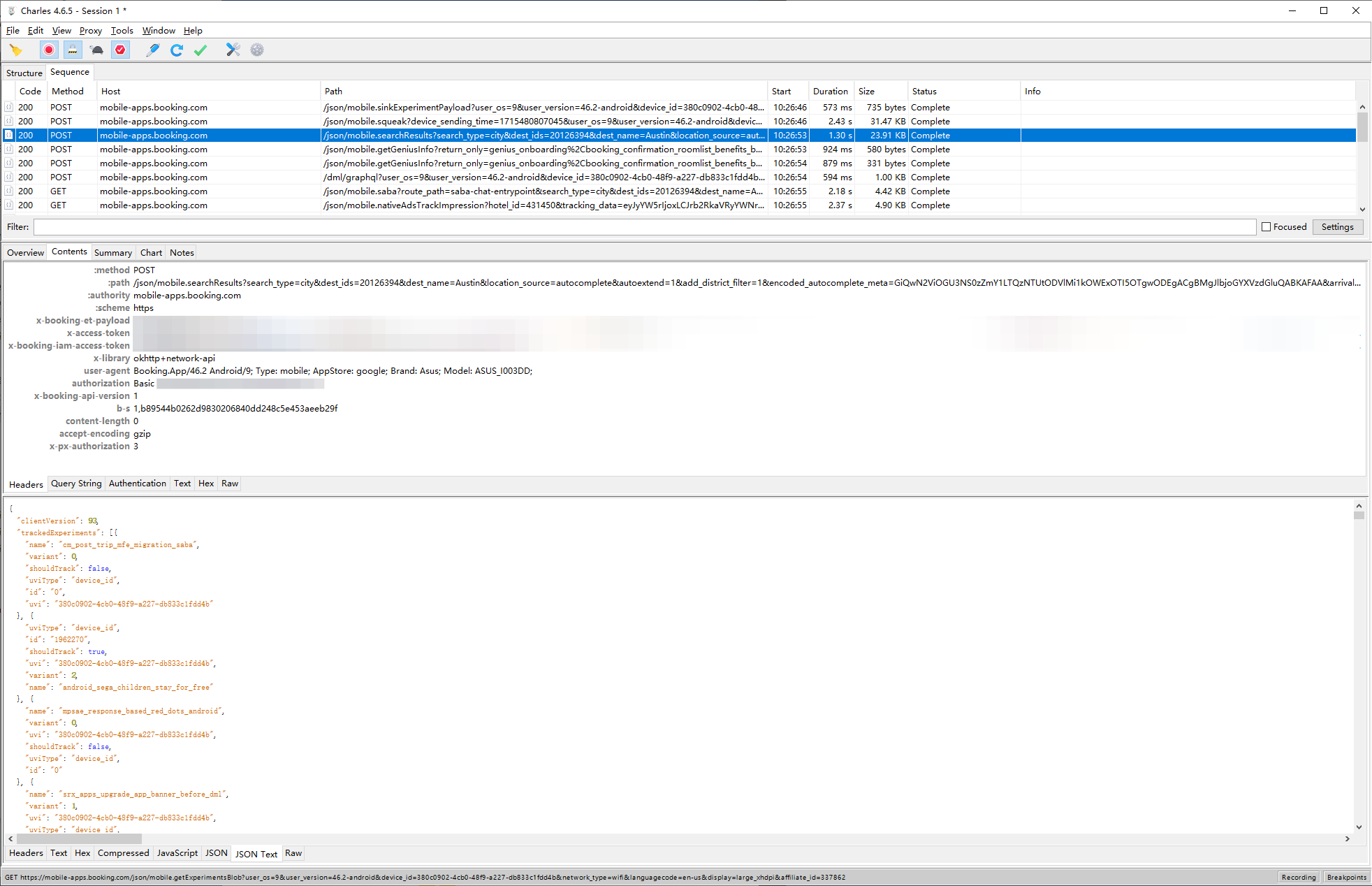
References

 Google Local Services API
Google Local Services API
 Baidu Search API
Baidu Search API
 Bing Search API
Bing Search API
 DuckDuckGo Search API
DuckDuckGo Search API
 Ebay Search API
Ebay Search API
 Walmart Search API
Walmart Search API
 The Home Depot Search API
The Home Depot Search API
 Naver Search API
Naver Search API
